2022巅峰极客复现 [Misc]easy_Forensic 题目描述 小明不小心把自己出题的flag在微信中发了出去,你能找到这个flag吗?
附件下载:https://pan.baidu.com/share/init?surl=ttL3WmlMn48RDXGCIy6VkQ 提取码(GAME)
步骤 下载附件是一个.raw文件,内存取证题
利用取证工具volatility(一般kali自带volatility,但2022版的kali需要自行安装)
1、查看镜像系统 volatility -f secret.raw imageinfo
┌──(root㉿kali)-[~/桌面] └─# volatility -f secret.raw imageinfo Volatility Foundation Volatility Framework 2.6 INFO : volatility.debug : Determining profile based on KDBG search... Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_23418 AS Layer1 : WindowsAMD64PagedMemory (Kernel AS) AS Layer2 : FileAddressSpace (/root/桌面/secret.raw) PAE type : No PAE DTB : 0x187000L KDBG : 0xf80003fef070L Number of Processors : 1 Image Type (Service Pack) : 0 KPCR for CPU 0 : 0xfffff80003ff0d00L KUSER_SHARED_DATA : 0xfffff78000000000L Image date and time : 2022-08-13 11:48:11 UTC+0000 Image local date and time : 2022-08-13 19:48:11 +0800
支持的系统中有:Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_23418
#调出shell窗口,如果正确的话便可以getshell volatility -f 1.raw --profile=Win7SP1x64 volshell #shell命令: dt("内核关键数据结构名称") dt("_PEB")
得到正确的镜像系统后,便可以在后面加上
2、查看桌面的文件目录 volatility -f secret.raw --profile=Win7SP1x64 filescan |grep 'Desktop'
┌──(root㉿kali)-[~/桌面] └─# volatility -f secret.raw --profile=Win7SP1x64 filescan |grep 'Desktop' Volatility Foundation Volatility Framework 2.6 0x000000006c9c6290 16 0 R--rwd \Device\HarddiskVolume1\Users\Admin\Links\Desktop.lnk 0x000000006d526f20 8 0 R--r-d \Device\HarddiskVolume1\Users\Admin\Desktop\MRCv120.exe 0x0000000072e8bf20 2 0 -W-rw- \Device\HarddiskVolume1\Users\Admin\Desktop\EULAaccepted.dat 0x000000007d80a7d0 16 0 R--r-- \Device\HarddiskVolume1\Users\Admin\Desktop\gift.jpg 0x000000007d84af20 15 0 R--rw- \Device\HarddiskVolume1\Users\Admin\Desktop\hint.txt 0x000000007d84e350 14 0 R--rw- \Device\HarddiskVolume1\Users\Admin\Desktop\secret.zip 0x000000007da64360 2 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Desktop.ini 0x000000007da66c70 16 0 R--rwd \Device\HarddiskVolume1\Users\Public\Desktop\desktop.ini 0x000000007da66dc0 2 0 R--rwd \Device\HarddiskVolume1\Users\Admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\Desktop.ini 0x000000007da68070 2 0 R--rwd \Device\HarddiskVolume1\Users\Admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Maintenance\Desktop.ini 0x000000007da68c00 2 0 R--rwd \Device\HarddiskVolume1\Users\Admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\Accessibility\Desktop.ini 0x000000007da6af20 2 0 R--rwd \Device\HarddiskVolume1\Users\Admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\System Tools\Desktop.ini 0x000000007da6dab0 2 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Maintenance\Desktop.ini 0x000000007da6fab0 2 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Accessibility\Desktop.ini 0x000000007da6fc00 2 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\System Tools\Desktop.ini 0x000000007da704a0 2 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Tablet PC\Desktop.ini 0x000000007da7f310 2 1 R--rwd \Device\HarddiskVolume1\Users\Admin\Desktop 0x000000007da7f4e0 2 1 R--rwd \Device\HarddiskVolume1\Users\Admin\Desktop 0x000000007da80740 16 0 R--rw- \Device\HarddiskVolume1\Users\Public\Desktop\Glary Tracks Eraser.lnk 0x000000007da81670 2 1 R--rwd \Device\HarddiskVolume1\Users\Public\Desktop 0x000000007da81b70 2 1 R--rwd \Device\HarddiskVolume1\Users\Public\Desktop 0x000000007dae0420 10 0 R--rw- \Device\HarddiskVolume1\Users\Admin\Desktop\wechat.txt 0x000000007dc47bc0 2 0 R--rwd \Device\HarddiskVolume1\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Remote Desktop Connection.lnk 0x000000007de7c070 11 0 R--r-d \Device\HarddiskVolume1\Users\Admin\Desktop\MRCv120.exe 0x000000007dfa9150 9 0 R--r-d \Device\HarddiskVolume1\Users\Admin\Desktop\MRCC206.tmp 0x000000007e144d20 16 0 R--rwd \Device\HarddiskVolume1\Users\Admin\Desktop\desktop.ini 0x000000007e614420 1 1 R--rw- \Device\HarddiskVolume1\Users\Admin\Desktop 0x000000007ee47230 16 0 R--rw- \Device\HarddiskVolume1\Users\Public\Desktop\Firefox.lnk 0x000000007f1e6ad0 1 1 -W-r-- \Device\HarddiskVolume1\Users\Admin\Desktop\111.raw
发现其中几个比较显眼的
0x000000007d80a7d0 16 0 R--r-- \Device\HarddiskVolume1\Users\Admin\Desktop\gift.jpg 0x000000007d84af20 15 0 R--rw- \Device\HarddiskVolume1\Users\Admin\Desktop\hint.txt 0x000000007d84e350 14 0 R--rw- \Device\HarddiskVolume1\Users\Admin\Desktop\secret.zip 0x000000007dae0420 10 0 R--rw- \Device\HarddiskVolume1\Users\Admin\Desktop\wechat.txt
注:查看记事本隐藏消息
volatility -f secret.raw --profile=Win7SP1x86 editbox
查看剪贴板消息
volatility -f secret.raw --profile=Win7SP1x64 clipboard
提取进程memdump
volatility -f secret.raw --profile=Win7SP1x64 memdump -p xxx --dump-dir=./ memdump:提取出指定进程,常用foremost 来分离里面的文件
查看cmd命令行消息
volatility -f secret.raw --profile=Win7SP1x64 cmdscan
3、提取所需文件(其中hint.txt无法提取) volatility -f secret.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000007d80a7d0 --dump-dir=./ 注: -Q的参数为内存地址 --dump-dir的参数为导出文件的目录
┌──(root㉿kali)-[~/桌面] └─# volatility -f secret.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000007d80a7d0 --dump-dir=./ Volatility Foundation Volatility Framework 2.6 DataSectionObject 0x7d80a7d0 None \Device\HarddiskVolume1\Users\Admin\Desktop\gift.jpg
输入命令后回车即可,提取出的文件会保存在桌面,共提取三个文件:gift.jpg、secret.zip、wechat.txt
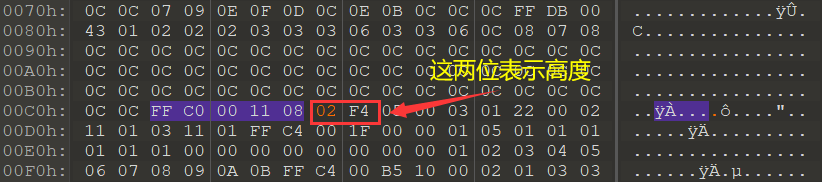
4、修改jpg图片高度 gift.jpg图片需要修改高度,用010editor打开图片搜索:FF C0 00 11 08
jpg图片的高度需修改FF C0 00 11 08字节的后两位
再次打开图片得到密码
Passwd:Nothing is more important than your life! 需修改成:Nothing_is_more_important_than_your_life!(服了)
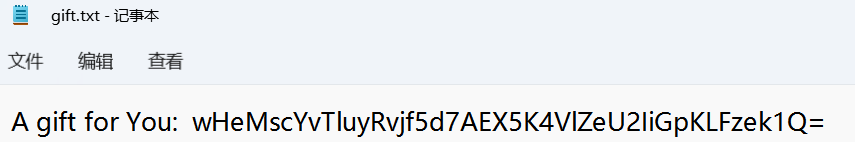
5、获取秘钥 用修改后的密码打开secret.zip中的加密文件
A gift for You: wHeMscYvTluyRvjf5d7AEX5K4VlZeU2IiGpKLFzek1Q=
加密的秘钥,直接base64是解不了的From Base64 + To Hex运行得到秘钥:
c0778cb1c62f4e5bb246f8dfe5dec0117e4ae15959794d88886a4a2c5cde9354
密文则是提取出来的wechat.txt,由于微信的数据库采用SQLite加密,根据我们已经获得的密钥,可以尝试使用openssl解密。
6、解密脚本 解密部分参考大佬的博客:https://blog.7herightp4th.top/index.php/archives/22/
里面有完整的pc微信数据库的解密脚本,换一下路径和password即可
from Crypto.Cipher import AESimport hashlib, hmac, ctypesSQLITE_FILE_HEADER = bytes ("SQLite format 3" ,encoding='ASCII' ) + bytes (1 ) IV_SIZE = 16 HMAC_SHA1_SIZE = 20 KEY_SIZE = 32 DEFAULT_PAGESIZE = 4096 DEFAULT_ITER = 64000 password = bytes .fromhex("c0778cb1c62f4e5bb246f8dfe5dec0117e4ae15959794d88886a4a2c5cde9354" .replace(' ' ,'' )) with open (r'C:\Users\lenovo\Desktop\wechat' , 'rb' ) as f: blist = f.read() print (len (blist))salt = blist[:16 ] key = hashlib.pbkdf2_hmac('sha1' , password, salt, DEFAULT_ITER, KEY_SIZE) first = blist[16 :DEFAULT_PAGESIZE] mac_salt = bytes ([x^0x3a for x in salt]) mac_key = hashlib.pbkdf2_hmac('sha1' , key, mac_salt, 2 , KEY_SIZE) hash_mac = hmac.new(mac_key ,digestmod = 'sha1' ) hash_mac.update(first[:-32 ]) hash_mac.update(bytes (ctypes.c_int(1 ))) if (hash_mac.digest() == first[-32 :-12 ]): print ('Correct Password' ) else : raise RuntimeError('Wrong Password' ) blist = [blist[i:i+DEFAULT_PAGESIZE] for i in range (DEFAULT_PAGESIZE,len (blist),DEFAULT_PAGESIZE)] with open (r'C:\Users\lenovo\Desktop\flag.db' , 'wb' ) as f: f.write(SQLITE_FILE_HEADER) t = AES.new(key ,AES.MODE_CBC ,first[-48 :-32 ]) f.write(t.decrypt(first[:-48 ])) f.write(first[-48 :]) for i in blist: t = AES.new(key ,AES.MODE_CBC ,i[-48 :-32 ]) f.write(t.decrypt(i[:-48 ])) f.write(i[-48 :])
运行后得到flag.db文件,可以用记事本方式打开搜索flag即可。